Security Concepts - Mitigation Techniques
In today's digital landscape, where cyber threats continue to evolve and pose significant risks, protecting your server from potential attacks is of utmost importance. One effective approach to enhance security is through mitigation techniques. In this blog post, we will delve into what mitigation techniques are, how they are used, and provide an example of a mitigation technique to protect a server.
Understanding Mitigation Techniques:
Mitigation techniques refer to a set of proactive measures designed to reduce or eliminate potential risks and vulnerabilities that could compromise the security and integrity of a system or network. These techniques aim to mitigate the impact of security threats and minimize the likelihood of successful attacks.
Common Types of Mitigation Techniques:
Access Control:
Access control mechanisms are crucial for restricting unauthorized access to your server. This technique involves implementing stringent user authentication processes, such as strong passwords, multi-factor authentication (MFA), and role-based access control (RBAC). By enforcing access control, you ensure that only authorized individuals can gain entry to sensitive data or system resources.
Encryption:
Encryption is a fundamental technique used to secure data both at rest and in transit. It involves converting plaintext information into ciphertext using encryption algorithms. By employing encryption, even if an attacker manages to intercept the data, it remains incomprehensible without the decryption key. Transport Layer Security (TLS) and FileVault are examples of encryption techniques commonly used to protect server communications and data storage, respectively.
Intrusion Detection and Prevention Systems (IDPS):
IDPSs are designed to monitor network traffic and identify potential intrusions or malicious activities. These systems use various methods, such as signature-based detection, anomaly detection, and behavioral analysis, to detect and respond to security incidents promptly. IDPSs play a critical role in mitigating potential threats by alerting administrators or automatically blocking suspicious traffic.
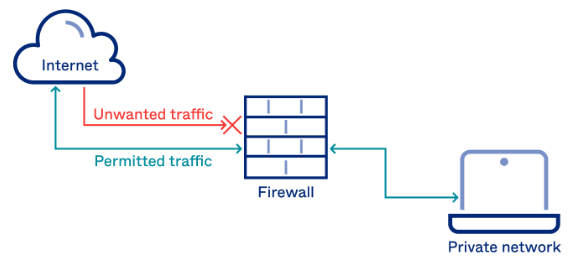
Firewalls:
Firewalls act as a barrier between your server and external networks, filtering incoming and outgoing traffic based on predetermined rules. They monitor and control network traffic flow, preventing unauthorized access and filtering out potentially malicious packets. Firewalls can be implemented at the network level (hardware or software-based) or on individual systems to provide an added layer of protection.
Example of a Mitigation Technique: Protecting a Server:
The common mitigation technique for protecting a server. are the implementation of multiple layers of security measures, including firewalls, intrusion detection systems, and encryption.
Steps for Implementation:
To protect your server, follow these steps:
- Deploy a firewall to filter and control incoming and outgoing traffic.
- Implement an intrusion detection system to monitor network activity and detect potential threats.
- Utilize encryption techniques to secure sensitive data and communications.
- Regularly update and patch your server's operating system and software to address vulnerabilities.
- Conduct regular security audits and vulnerability assessments to identify and remediate any weaknesses.
Conclusion:
Mitigation techniques are vital for safeguarding your server and mitigating potential security risks. By implementing robust access controls, encryption mechanisms, intrusion detection systems, and firewalls, you create multiple layers of defense to protect your server from unauthorized access, data breaches, and malicious activities.
Remember to regularly update and patch your server's software and conduct security audits to stay ahead of emerging threats. By adopting these mitigation techniques, you can enhance the security posture of your server and minimize the chances of successful attacks.
In today's digital landscape, where cyber threats continue to evolve and pose significant risks, it is crucial to prioritize the implementation of mitigation techniques to protect your server. By investing in security measures and staying vigilant, you can ensure the integrity and confidentiality of your server's data and operations.
Remember, security is an ongoing process, and it's essential to stay updated with the latest security best practices and emerging threats. By adopting a proactive approach to security and utilizing effective mitigation techniques, you can significantly reduce the risk of security incidents and maintain the trust of your users and clients.
Stay secure and protect your server with mitigation techniques. Safeguard your valuable assets, and let security be the foundation of your digital success.
















0 comments:
Post a Comment