AP and WLC management access connections
The Control and Provisioning of Wireless Access Points (CAPWAP)
The Control and Provisioning of Wireless Access Points (CAPWAP) is a protocol used in split-mac wireless architectures to manage access points (APs) in a centralized manner. It is a lightweight protocol that allows for secure communication between the wireless LAN controller and the APs. CAPWAP is used in wireless networks that employ a centralized controller, and it provides a number of advantages over other management protocols.
In a CAPWAP-enabled wireless network, the APs are split into two logical components: the Control and Provisioning of Wireless Access Points (CAPWAP) protocol and the Access Point Protocol (APP). The CAPWAP protocol is responsible for the centralized management of the network, while the APP handles the data traffic.
Advantages of CAPWAP:
With CAPWAP, adding new APs to a wireless network is a simple process. The administrator can configure the new APs from the centralized controller, and they will automatically join the network.
CAPWAP provides a high level of security, ensuring that all communication between the APs and the controller is encrypted and secure.
How CAPWAP Works:
When an AP is powered on and connected to the network, it sends a discovery request message to the network, looking for a WLC. The AP can use various methods to discover the WLC, including Domain Name System (DNS) resolution, Dynamic Host Configuration Protocol (DHCP) option 43, or a locally stored IP address.
Once the AP discovers the WLC, it sends a join request message to the WLC. The WLC will then send a join response message to the AP, which includes the configuration parameters for the AP, such as the SSIDs and security policies. The AP will then establish a CAPWAP tunnel with the WLC over the UDP port 5246. This tunnel is used to carry all the CAPWAP messages between the AP and the controller.
The CAPWAP protocol has several message types, including Discovery, Join, Configuration, and Data. The Discovery message type is used by the AP to discover the WLC, while the Join message type is used to join the network. The Configuration message type is used to configure the APs, and the Data message type is used to transmit the wireless frames between the AP and the WLC.
Protocol and Port:
CAPWAP operates on the transport layer of the OSI model and uses the User Datagram Protocol (UDP) on port 5246 and 5247 for encrypted and unencrypted traffic respectively. The CAPWAP protocol encapsulates the wireless frames and sends them over the network to the WLC, which de-encapsulates the frames and forwards them to the wired network.
Conclusion
In summary, CAPWAP is a protocol used in split-mac wireless architectures to provide centralized management of APs in a wireless network. It provides a number of advantages, including centralized management, scalability, and security. CAPWAP works by splitting the AP into two logical components, the CAPWAP protocol and the APP, and establishing a CAPWAP tunnel between the AP and the controller for communication.
Compare Cisco Wireless Architectures
Compare Cisco Wireless Architectures
When it comes to designing and deploying wireless networks, Cisco provides a variety of architectures that suit different needs and environments. In this article, we will explore three of the most common Cisco wireless architectures: Autonomous AP architecture, Split-MAC architecture (including CAPWAP), and Cloud-Based architecture.
Autonomous AP Architecture:
Autonomous Access Point (AP) architecture is the traditional approach of deploying wireless networks. In this architecture, each AP operates independently and performs all the functions needed to manage wireless clients, security, and Quality of Service (QoS). This type of architecture is best suited for small to medium-sized networks, where there are no centralized management requirements.
Each autonomous AP must be configured with a management IP address so that it can be remotely accessed using SSH or a web interface. Each AP must be individually managed.
This is how typical autonomous AP's are connected.
Key Points:
Each AP performs all the functions needed to manage wireless clients, security, and QoS.
This architecture is best suited for small to medium-sized networks.
Split-MAC Architecture:
Split-MAC architecture is the most common architecture used in modern wireless networks. In this architecture, the AP is split into two logical components: the Control and Provisioning of Wireless Access Points (CAPWAP) protocol and the Access Point Protocol (APP). The CAPWAP protocol is responsible for the centralized management of the network, while the AP handles the data traffic.
We will discuss CAPWAP in detail in a different Article
Key Points:
AP is responsible for handling client traffic.
This architecture is best suited for large-scale networks.
Cloud-Based Architecture:
Cloud-Based architecture is the latest trend in wireless networking. In this architecture, the management and control of the network are moved to the cloud. The APs are controlled by a cloud-based controller, which provides a centralized view of the entire network. This architecture is best suited for environments where there are many remote sites, and it requires little to no on-site management.
Key Points:
APs are controlled by a cloud-based controller.
The controller provides a centralized view of the entire network.
This architecture is best suited for environments with many remote sites.
Conclusion:
Choosing the right wireless architecture depends on the needs of the organization. Autonomous AP architecture is suitable for small to medium-sized networks, while Split-MAC architecture is ideal for large-scale networks. Cloud-Based architecture is a new approach that is suitable for organizations with many remote sites. As the demand for wireless networks continues to grow, Cisco will continue to provide new and innovative architectures that suit different needs and environments.
Native Vlan
Native Vlan
Introduction:
What are Native VLANs?
Native VLAN Configuration:
Switch(config)# interface GigabitEthernet0/1
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk native vlan 10
Switch(config-if)# end
Native VLAN Verification:
Example Use Case:
Conclusion:
Port-Channels
Port-Channels
A port channel, also known as a link aggregation group or channel group, is a technology that allows multiple physical interfaces to be grouped together into a single logical interface.
This logical interface is used to increase the bandwidth, provide redundancy, and improve the reliability of the network. PortChannels are commonly used in enterprise networks to increase the capacity of the network and to provide redundancy in the event of a link failure. There are several types of PortChannels, including Static PortChannels, Port Aggregation Protocol (PaGP), and Link Aggregation Protocol (LACP). In this blog post, we will discuss each of these types in detail, including their configuration and verification.
Static PortChannel
The "Static" mode is a configuration in which the link aggregation is manually configured without using any protocol such as LACP or PAGP. It is similar to the "On" mode but requires manual configuration on both ends of the link, rather than relying on the ports to be always enabled for link aggregation. This mode is often used in situations where LACP or PAGP is not available or cannot be used
Configuration
- Configure the physical interfaces as L2 or L3 access or trunk ports.
- Create a PortChannel interface and assign a channel number.
- Add the physical interfaces to the PortChannel interface.
Switch(config-if-range)# channel-group 1 mode on
Switch(config-if-range)# switchport mode trunk
Switch(config)# interface Port-Channel 1
Switch(config-if)# switchport mode trunk
Switch(config-if)# spanning-tree portfast trunk
Switch(config-if)# exit
Verification
Link Aggregation Protocol (LACP)
Link Aggregation Control Protocol (LACP) is a standards-based protocol that also dynamically groups multiple physical links into a single logical link. LACP uses a negotiation process to determine if a potential PortChannel partner is capable of supporting LACP. If the partner is capable, LACP will attempt to form a PortChannel. If the partner is not capable, LACP will not form a PortChannel.
Configuration
To configure LACP, follow these steps:
- Configure the physical interfaces as L2 or L3 access or trunk ports.
- Enable LACP on the physical interfaces.
- Create a PortChannel interface and assign a channel number.
Here is an example configuration for an LACP PortChannel using two physical interfaces (Ethernet 1/1 and Ethernet 1/2) and channel number 1:
Switch(config-if-range)# switchport mode trunk
Switch(config-if-range)# channel-group 1 mode active
Switch(config-if-range)# exit
Switch(config)# interface Port-Channel 1
Switch(config-if)# switchport mode trunk
Switch(config-if)# spanning-tree portfast trunk
Switch(config-if)# exit
Modes in LACP
Verification
Switch# show etherchannel summary
Port Aggregation Protocol (PaGP)

Configuration
- Configure the physical interfaces as L2 or L3 access or trunk ports.
- Enable PaGP on the physical interfaces.
- Create a PortChannel interface and assign a channel number.
Switch(config)# interface range Ethernet 1/1 - 2
Switch(config-if-range)# switchport mode trunk
Switch(config-if-range)# channel-group 1 mode desirable
Switch(config-if-range)# exit
Switch(config)# interface Port-Channel 1
Switch(config-if)# switchport mode trunk
Switch(config-if)# spanning-tree portfast trunk
Switch(config-if)# exit
Modes in PaGP
Verification
Switch# show etherchannel summary
Conclusion
CDP & LLDP
Configure and verify Layer 2 discovery protocols (Cisco Discovery Protocol and LLDP)
CDP and LLDP are layer 2 discovery protocols that enable different network devices to automatically discover each other. This allows devices to exchange information such as hostname, IP and MAC address, connected interfaces, and device capabilities. While CDP is a proprietary protocol developed by Cisco, LLDP is an open-source protocol supported by multiple vendors.
CDP allows a device to learn about its neighbors on directly connected interfaces. A device can retrieve information about its neighbors such as their hostname, IP and MAC addresses, and device capabilities. To check CDP status, we can use the command "show cdp" and "show cdp neighbors" to view the list of neighboring devices.
On the other hand, LLDP also enables devices to discover their neighbors on directly connected interfaces. By default, LLDP is disabled on all interfaces, and we must manually enable it on interfaces that require it. We can use the "lldp run" command to enable LLDP, and "show lldp neighbors" to view the neighboring devices and LLDP is an open-source protocol.
The difference between CDP and LLDP is that LLDP does not identify the neighbor's platform or IGMP capabilities. Also, CDP lists a neighbor's capabilities whether they are enabled or not, while LLDP only lists a neighbor's capabilities when they are enabled.
Both CDP and LLDP have a timer that sends messages and a hold time after which they remove a neighbor from their list. To change the CDP or LLDP time, we can use the commands
"cdp timer <seconds>" and "cdp holdtime <seconds>" for CDP and
"lldp timer <seconds>" and "lldp holdtime <seconds>" for LLDP.
CDP Configuration and Verification Commands
To enable CDP on a device:
conf t
cdp run
To disable CDP on an interface:
no cdp enable
To display CDP information:
show cdp neighbors
The show cdp neighbors command displays information about directly connected Cisco devices discovered by CDP. This includes device ID, local interface, hold time, and capabilities.show cdp neighbors detail
The show cdp neighbors detail command provides detailed information about the directly connected Cisco devices discovered by CDP, including IP address and platform information.show cdp interface [interface-name]
show cdp traffic
LLDP Configuration and Verification Commands
To enable LLDP on a device:
conf t
lldp run
To disable LLDP on an interface:
no lldp receive
To display LLDP information:
show lldp neighbors
The show lldp neighbors command displays information about directly connected devices discovered by LLDP. This includes the device ID, local interface, and capabilities.
show lldp neighbors detail
The show lldp neighbors detail command provides detailed information about the directly connected devices discovered by LLDP, including system name, system description, and management address.
show lldp traffic
The show lldp traffic command displays information about the LLDP packets being sent and received on a device.
show lldp interface [interface-name]
The show lldp interface [interface-name] command displays LLDP information for a specific interface on a device, including the LLDP hold time and the version of LLDP being used
In conclusion, CDP and LLDP are essential protocols that enable network devices to discover each other on directly connected interfaces. They provide valuable information about neighboring devices and their capabilities, which helps network administrators to troubleshoot and manage their networks effectively. By using the show commands mentioned above, network administrators can easily view CDP or LLDP information, including device ID, local interface, and capabilities, to better understand the devices on their network. The output generated by these show commands can be used for troubleshooting and network management purposes.
Trunk ports
Inter-switch connectivity - Trunk ports
For example, to add VLAN 40 to the list of allowed VLANs:
Configure and verify VLANs
Configure and verify VLANs
Virtual Local Area Networks (VLANs) enable network administrators to segment a LAN into smaller, independent networks to improve network efficiency, security, and performance. In this blog post, we will look at how to configure and verify VLANs that span multiple switches.
Create VLANs on each switch:
Assign switch ports to the VLAN:
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 10
Verify the VLAN configuration:
Access ports (data and voice):
Switch(config)# interface GigabitEthernet1/0/2
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 20
Switch(config-if)# switchport voice vlan 30
In the above example, the access port is assigned to VLAN 20 for data traffic and VLAN 30 for voice traffic.
Here's an example of how an access port might work in a real-world scenario:
Configuring and verifying IPv6 addressing
Configuring and verifying IPv6 addressing
As the demand for IP addresses continues to grow, IPv6 has become increasingly important in modern networking. Configuring and verifying IPv6 addressing and prefix is a critical task for network administrators. In this blog post, we'll explore the necessary steps and considerations for configuring and verifying IPv6 addressing and prefix.
IPv6 Addressing:
Version (4 bits): This field indicates the IP version number. For IPv6 packets, the value is 6.
Traffic Class (8 bits): This field is used to classify and prioritize packets. It includes a 6-bit Differentiated Services Code Point (DSCP) field and a 2-bit Explicit Congestion Notification (ECN) field.
Flow Label (20 bits): This field is used to identify packets belonging to a specific flow. A flow is a sequence of packets that have the same source and destination IP addresses, the same protocol, and the same source and destination port numbers.
Payload Length (16 bits): This field specifies the length of the payload (data) in the packet.
Next Header (8 bits): This field specifies the type of the next header following the IPv6 header. This can be a transport layer protocol such as TCP or UDP, or another protocol.
Hop Limit (8 bits): This field is similar to the Time to Live (TTL) field in IPv4 packets. It specifies the maximum number of hops that the packet can take before being discarded.
Source Address (128 bits): This field specifies the source IPv6 address of the packet.
Destination Address (128 bits): This field specifies the destination IPv6 address of the packet.
Here's a new example of configuring and verifying IPv6 addressing and prefix:
Assume that we have two Cisco routers, R1 and R2, connected to each other via a serial link. We want to configure the following IPv6 addresses on the interfaces:
R1:
IPv6 address: 2001:DB8:1:1::1/64
R2:
IPv6 address: 2001:DB8:1:1::2/64
To configure the IPv6 addresses, we can follow these steps:
Step 1: Enable IPv6 routing on both routers using the global configuration command:
R1(config)#ipv6 unicast-routing
R2(config)#ipv6 unicast-routing
Step 2: Configure the IPv6 global unicast address on the GigabitEthernet0/0 interfaces of both routers using the interface configuration command:
R1(config)#interface GigabitEthernet0/0
R1(config-if)#ipv6 address 2001:DB8:1:1::1/64
R2(config)#interface GigabitEthernet0/0
R2(config-if)#ipv6 address 2001:DB8:1:1::2/64
Step 3: Verify that the IPv6 addresses have been configured correctly by using the "show ipv6 interface" command:
GigabitEthernet0/0 is up, line protocol is up
IPv6 is enabled, link-local address is FE80::1
Global unicast address(es):
2001:DB8:1:1::1, subnet is 2001:DB8:1:1::/64
Joined group address(es):
FF02::1
FF02::2
FF02::1:FF00:1
MTU is 1500 bytes
GigabitEthernet0/0 is up, line protocol is up
IPv6 is enabled, link-local address is FE80::2
Global unicast address(es):
2001:DB8:1:1::2, subnet is 2001:DB8:1:1::/64
Joined group address(es):
FF02::1
FF02::2
FF02::1:FF00:2
MTU is 1500 bytes
From the output above, we can see that the IPv6 addresses have been configured correctly. The link-local addresses have been automatically configured and the global unicast addresses are in the same subnet. We can also see the subnet mask (/64) and the joined group addresses.
To test the connectivity between the routers using ping, we can use the following command on R1:
R1#ping ipv6 2001:DB8:1:1::2
Sending 5, 100-byte ICMP Echos to 2001:DB8:1:1::2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
The output above confirms that the IPv6 addresses have been configured correctly and the routers can communicate with each other using IPv6.
In addition to configuring and verifying IPv6 addressing and prefix on individual devices, network administrators should also ensure that all network devices such as routers, switches, and firewalls are properly configured with the correct IPv6 addressing and prefix settings. This will help ensure that all devices on the network can communicate with each other and access external resources such as the Internet.
Verify IP parameters for Client OS (Windows, Mac OS, Linux)
Verify IP parameters for Client OS
Windows:
Mac OS:
Linux:
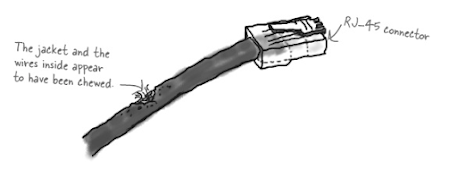
Identifying Interface and Cable Issues in Network Engineering
Identifying Interface and Cable Issues in Network Engineering
Collisions:
Troubleshooting Collisions:
Errors:
Troubleshooting Errors:
Duplex Mismatch:
Troubleshooting Duplex Mismatch:
Speed Issues:
Troubleshooting Speed:
OSPF Cheat sheet
OSPF Cheat Sheet
OSPF (Open Shortest Path First) is a popular routing protocol used in many large enterprise networks. This protocol is designed to distribute routing information within a single autonomous system (AS) in a scalable and efficient manner. OSPF is a classless routing protocol, which means that it supports variable-length subnet masks (VLSMs), route summarization, and hierarchical network design. In this article, we'll provide a cheat sheet for OSPF that covers the most important concepts and components of the protocol.
OSPF Headers:
OSPF packets contain several different headers that provide information about the packet's origin, destination, and contents. Some of the key headers used in OSPF packets include:
• OSPF header: Provides information about the packet's length, type, and the source of the packet.
• LSA header: Provides information about the type and length of the LSA (Link State Advertisement) being carried by the packet.
• Router ID header: Specifies the unique identifier of the router that originated the packet.
Packet Type:
OSPF packets are categorized into several different types, each of which serves a specific purpose. Some of the most important types of OSPF packets include:
• Hello packets: Used to establish and maintain adjacencies between OSPF routers.
• Database Description (DBD) packets: Used to exchange information about the contents of the OSPF link-state database between routers.
• Link-State Request (LSR) packets: Used to request specific LSAs from other routers.
• Link-State Update (LSU) packets: Used to distribute LSAs to other routers.
Algorithm:
OSPF uses the Dijkstra algorithm to calculate the shortest path to each destination network. This algorithm considers the cost of each link in the network, as well as the available bandwidth, to determine the most efficient path.
Metric:
The metric used by OSPF to determine the cost of a link is referred to as the OSPF Cost. This value is calculated based on the bandwidth of the link and is used by the Dijkstra algorithm to determine the shortest path to each destination network.
AD:
The Administrative Distance (AD) is a value that specifies the trustworthiness of a routing protocol. In OSPF, the AD is set to 110, which is lower than most other routing protocols and indicates that OSPF is a highly reliable protocol.
Standard:
OSPF is an Internet Engineering Task Force (IETF) standard, which means that it is widely supported and standardized across the industry. This makes OSPF an attractive option for large enterprises that require a scalable and reliable routing protocol.
Multicast Addresses Used by OSPF:
OSPF uses several different multicast addresses to send and receive information between routers. Some of the most important multicast addresses used by OSPF include:
• All OSPF routers: 224.0.0.5
• Designated Router (DR): 224.0.0.6
• Backup Designated Router (BDR): 224.0.0.5
LSA Types:
LSAs are the building blocks of the OSPF link-state database. There are several different types of LSAs, each of which provides information about different aspects of the network. Some of the most important LSA types include:
• Router LSA: Provides information about the interfaces and neighbors of a router.
• Network LSA: Provides information about the routers attached to a network.
• Summary LSA: Provides information about the routes summarized by an area border router.
• External LSA: Provides information about routes that are external to the OSPF AS.
• Type 7 LSA: Used in Not-So-Stubby Areas (NSSA) to propagate external routes into the area.
OSPF Metric Formula:
The OSPF metric is calculated using the following formula:
• Cost = Reference Bandwidth / Bandwidth of the Interface
• The reference bandwidth is set to 100 Mbps by default, but can be changed if needed.
OSPF Neighbor States:
OSPF routers use Hello packets to establish and maintain adjacencies with their neighbors. There are several different states that a neighbor relationship can be in, including:
• Down: The neighbor relationship has not yet been established.
• Init: The router has received a Hello packet from the neighbor, but has not yet sent a Hello packet in response.
• 2-Way: The router has received a Hello packet from the neighbor and has sent a Hello packet in response.
• Exstart: The router and its neighbor are in the process of negotiating the contents of the DBD packets.
• Exchange: The router and its neighbor are exchanging DBD packets to build their link-state databases.
• Loading: The router is in the process of calculating its routing table based on the information in its link-state database.
• Full: The router has completed the process of calculating its routing table and is fully adjacent with its neighbor.
DR/BDR Election:
In OSPF, a Designated Router (DR) and a Backup Designated Router (BDR) are elected for each broadcast network. The DR is responsible for generating and distributing LSAs, while the BDR serves as a backup in case the DR fails. The election of the DR and BDR is based on the router ID, with the highest router ID being elected as the DR and the second highest being elected as the BDR.
External Route Types:
In OSPF, there are two different types of external routes: Type 1 and Type 2. Type 1 external routes have a higher metric than Type 2 external routes, making Type 2 routes preferred by default. The choice between Type 1 and Type 2 can be controlled using route-maps or other means.
OSPF Virtual Link:
A virtual link is a logical connection between two areas that allows for communication between routers that are not directly connected. Virtual links are used to connect a stub area to the rest of the OSPF AS when a physical connection is not possible.
Types of Routes Allowed in Each OSPF Area:
• In OSPF, each area has its own separate link-state database and operates independently of other areas. However, there are restrictions on the types of routes that can be allowed in each area. Some areas, such as the backbone area, can contain both intra-area and inter-area routes, while others, such as stub areas, can only contain intra-area routes.
Here is a basic example of how to configure OSPF on a Cisco router:
Router(config-router)# network [network-number] [wildcard-mask] area [area-number]
Router(config-router)# passive-interface default
Router(config-router)# no passive-interface [interface-name]
Router(config-router)# end
Basic Troubleshooting Steps to Configure OSPF:
• Verify that the correct interfaces are being included in the OSPF process.
• Check the status of the OSPF adjacencies using the show ip ospf neighbor command.
• Use the show ip ospf database command to check the contents of the link-state database.
• Check for errors in the OSPF logs using the show logging command.
• Verify that the correct OSPF hello and dead intervals are set for each interface.
• Ensure that the OSPF router ID is unique for each router in the network.
• If you are experiencing slow convergence, check the SPF timers and adjust if necessary.
• If virtual links are being used, verify that the correct configuration has been applied to both ends of the virtual link.
• Check for any Access Control List (ACL) or firewall rules that may be blocking OSPF packets.